Plugins are a huge part of why WordPress is the world’s leading Content Management System (CMS). However, they also add code to your website, providing more opportunities for vulnerability exploits.
Thankfully, there are ways to protect your WordPress site against malicious activity. With the right tools and techniques, you can defend against the 4.3 billion attempts to exploit vulnerabilities that take place every year.
In this article, we’ll look at what vulnerability exploits are and why they’ve been making headlines recently. We’ll then share three steps you can take to protect your WordPress site against related attacks. Let’s dive on in!
Understanding vulnerability exploits (and why they’re bad news for your WordPress website)
Recently, four major vulnerabilities were discovered in the popular form building plugin, Ninja Forms. A malicious third party could potentially use these loopholes to perform all manner of malicious activities.
Some possible attacks in the case of Ninja Forms included setting up redirects so anyone who attempts to access your site is forwarded to a malicious page instead. There, the hacker might infect the visitor’s browser with malware, or attempt to steal their private information such as payment details. All of these actions could be disastrous for your reputation and result in a loss of trust amongst your audience.
Malicious parties might even use these vulnerabilities to deface your website or delete it entirely. If you haven’t created regular backups, you could potentially lose all your content with no hope of ever restoring it.
Thankfully, Ninja Forms acted fast and patched all the identified vulnerabilities with the release of version 3.4.34.1. However, this does highlight the threat that plugins can pose to your website, with evidence to suggest that almost all WordPress vulnerabilities are related to plugins.
Plugins can expose your site to a wide range of threats. However, vulnerability exploits are particularly common. According to a recent report, there were 4.3 billion attempts to take advantage of weak code from over 9.7 million unique IP addresses in 2020.
Vulnerability exploits are so common, that when WordFence examined four million websites it discovered that all of them had experienced at least one vulnerability exploit attempt. If you’re using any WordPress plugins, it’s vital that you take steps to protect your site against such attacks.
How to protect yourself against vulnerability exploits (3 key practices)
At the time of this writing, there are almost 4,000 known WordPress plugin vulnerabilities in the WPScan database. That’s why it’s so important to take measures to protect your site against vulnerability exploits, and ensure you’re using plugins safely. Here are three best practices to follow to keep your site secure.
1. Keep your plugins up to date
When a vulnerability is discovered, the plugin’s developer will often rush to fix the problem and release an update. This means that keeping your plugins up-to-date is the best way to safeguard against known exploits. If you fall behind, you could miss out on important security fixes and leave your site open to attack.
You can check for updates manually by navigating to Updates > Update Plugins inside your WordPress dashboard. However, this isn’t ideal if you run multiple websites.
You can update all your plugins across multiple websites using ManageWP. Simply log into your ManageWP dashboard and select Plugins. You can then click on the Updates tab to view all the tools that have new versions available:
However, this method still requires you to manually check your ManageWP dashboard. Since vulnerability exploits pose such a serious threat, we recommend scanning for available updates automatically.
To put your updates on auto-pilot, select the Scheduling tab in your ManageWP dashboard. You can then choose a time and date for ManageWP to scan for updates and install any that it discovers:
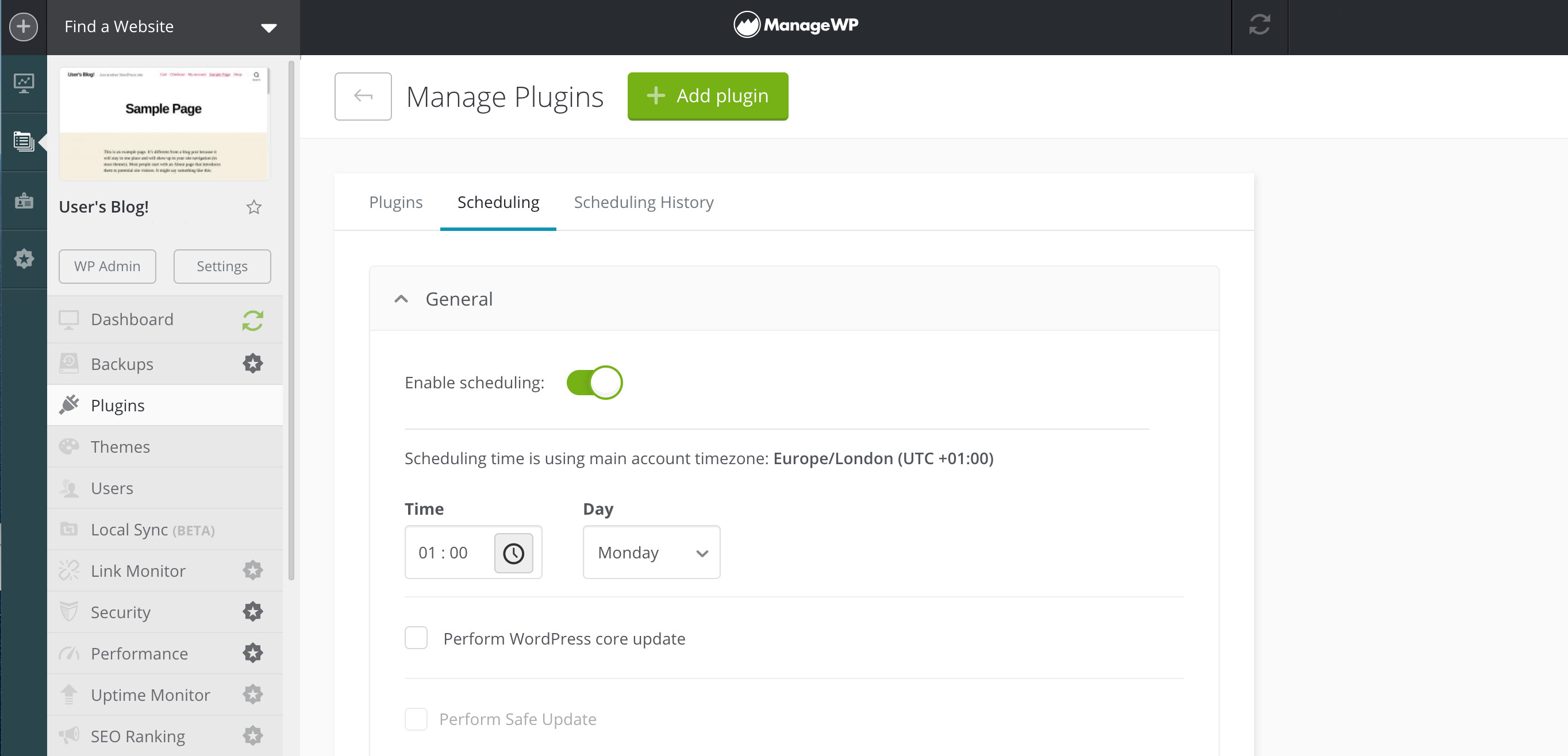
When it comes to auto-updating, some website owners are nervous about triggering plugin conflicts. If your site installs new updates automatically, there’s a chance that two plugins that previously co-existed happily may suddenly become incompatible while you’re not on-hand to resolve the issue.
With ManageWP’s Safe Updates, you can reap the benefits of auto-updates without having to worry about plugin conflicts. In the unlikely event that a problem does occur, our Safe Updates feature will roll back your changes and restore your website.
2. Use a Web Application Firewall (WAF)
When a vulnerability is discovered, the plugin’s developer will ideally issue a patch before it becomes public knowledge. However, this isn’t always the case, and there may be a period of time where you’re forced to use an insecure plugin.
In this scenario, a Web Application Firewall (WAF) can prevent attackers from abusing a known vulnerability by filtering out malicious requests before they reach your website. There are various firewalls available for WordPress, but Sucuri WAF is a popular option:
After purchasing your Sucuri WAF plan, you can log into your account and click on Protect My Site Now. You can then enter your domain name and choose whether you want to whitelist any directories. This can be useful for restricting access to vulnerable parts of your site that hackers frequently target, such as the admin directories.
You can also use Sucuri Domain Name System (DNS) as your DNS infrastructure. If you opt for this feature, Sucuri will perform geographic routing, which can deliver a performance boost. Although it won’t help keep your site safe, it can improve the visitor experience.
After editing these settings, you’ll need to scroll to the general dashboard page where Sucuri provides its DNS information. Your next task is changing the IP address for your website’s A record to point to Sucuri’s firewall. You can typically accomplish this via your domain registrar or DNS provider:
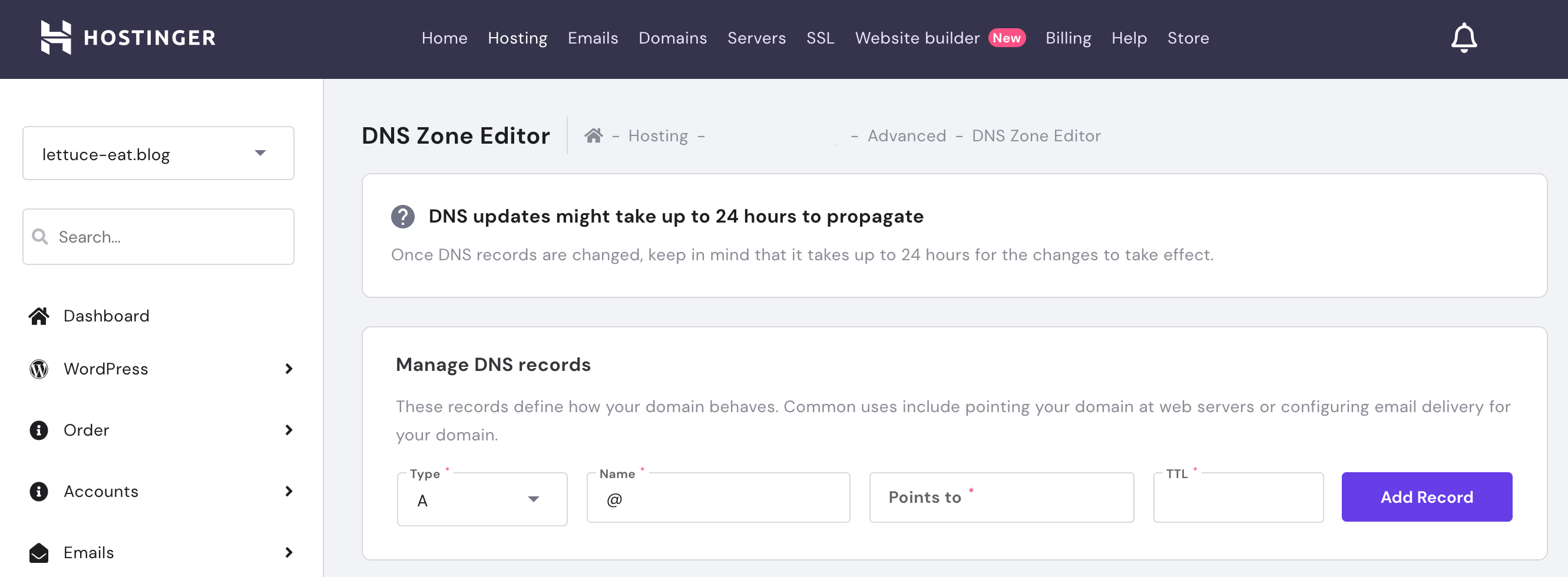
DNS changes can take up to 48 hours to propagate, although they’re typically completed within a few hours. You can check whether your DNS has propagated by visiting whatsmydns.net. Once it’s up-to-date, you’ll have the full protection of Sucuri’s firewall.
3. Stay informed about the latest WordPress vulnerabilities
If you’re going to protect yourself against vulnerability exploits, you need to know your site’s potential weak spots. There are lots of websites that post about WordPress security, including Security Boulevard, The Hacker News, and Help New Security.
By bookmarking these security-focused sites, you can keep up with the latest WordPress news, including known plugin vulnerabilities and patches. However, there are over 58,000 plugins available in the official WordPress Repository and many more in third-party marketplaces such as CodeCanyon. Monitoring thousands of plugins is no easy feat!
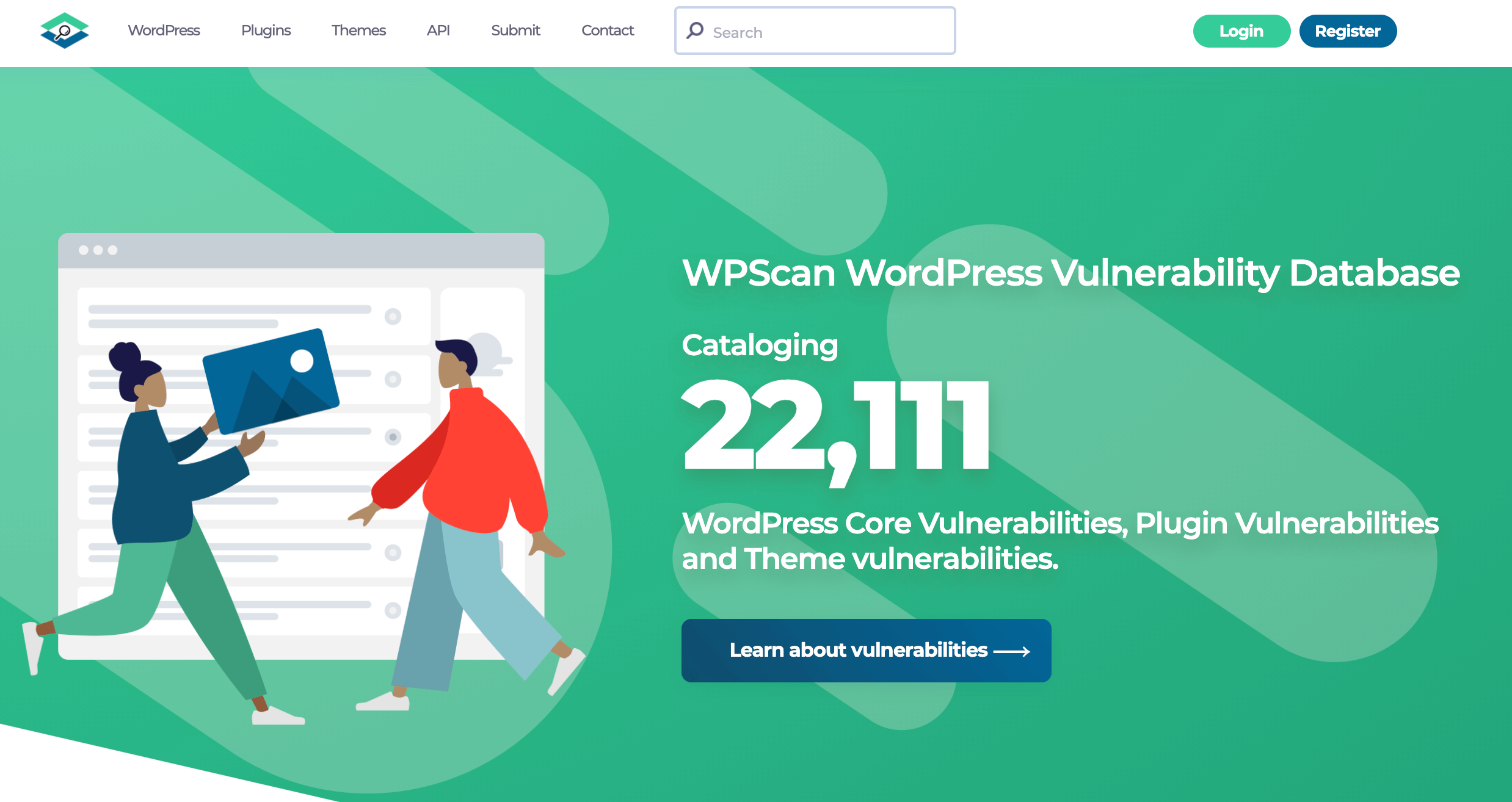
That’s why it helps to have some dedicated tools that can identify the vulnerabilities that pose a threat to your particular website. WPScan has published a publicly-available Vulnerability Database for WordPress Core, themes, and plugins:
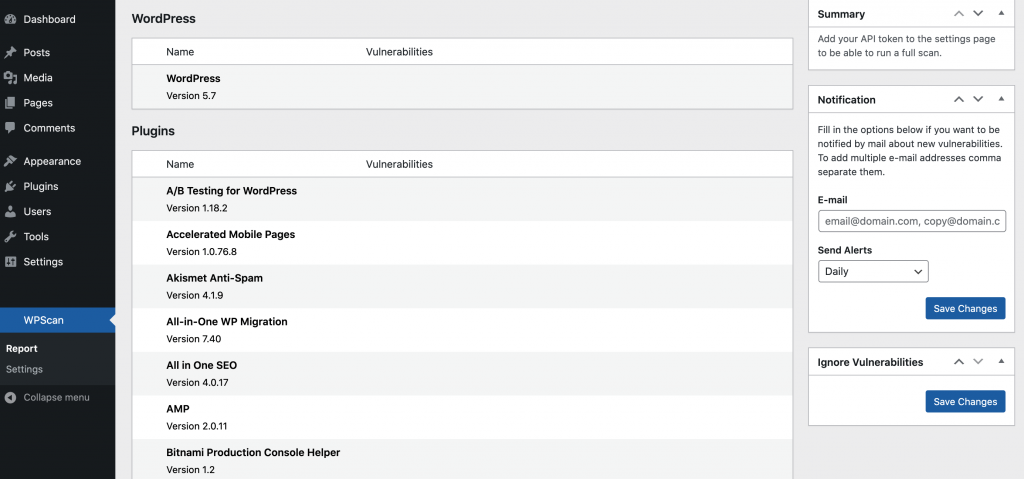
WPScan has even released a dedicated plugin that will scan your site for known plugin vulnerabilities:
 However, if you’re a ManageWP customer then you don’t need the WPScan plugin. We’ve collaborated with the WPScan team to display all their data directly inside your dashboard:
However, if you’re a ManageWP customer then you don’t need the WPScan plugin. We’ve collaborated with the WPScan team to display all their data directly inside your dashboard:
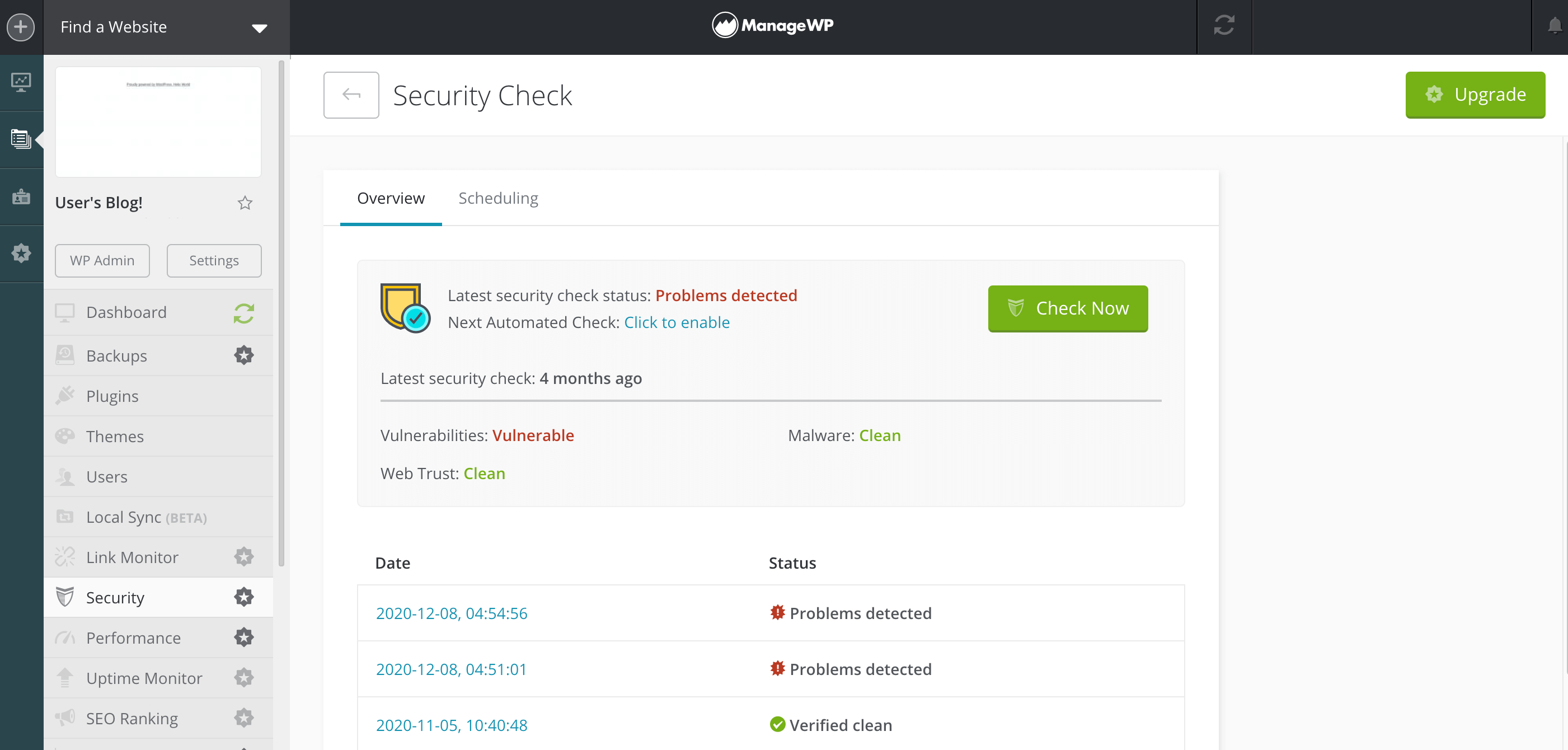
This Vulnerability Updates feature displays a notification alongside any plugins that have known vulnerabilities. Simply by glancing at your ManageWP dashboard, you can identify any issues that are currently impacting your plugins. You can then take steps to rectify this threat, such as installing the latest update or removing the plugin.
Conclusion
If your plugins contain vulnerabilities, then hackers can potentially exploit these weak points to wreak havoc on your site. By taking some precautions now, you can make it more difficult for malicious third parties to access your website, even when it’s running vulnerable code.
Let’s recap our three-step plan for defending against plugin-related attacks:
- Keep your plugins up to date.
- Use a Web Application Firewall (WAF) such as Sucuri WAF.
- Stay informed about the latest vulnerabilities.
Do you have any questions about how to protect against vulnerability exploits? Let us know in the comments section below!
Featured Image credit: Unsplash.
Keep reading the article at ManageWP. The article was originally written by Will Morris on 2021-04-27 11:00:29.
The article was hand-picked and curated for you by the Editorial Team of WP Archives.